Deep dive into Istio Ambient implement cross pods hub by network namespace trick
· ☕ 9 min read
Deep dive into Istio Ambient implement cross pods hub by network namespace trick
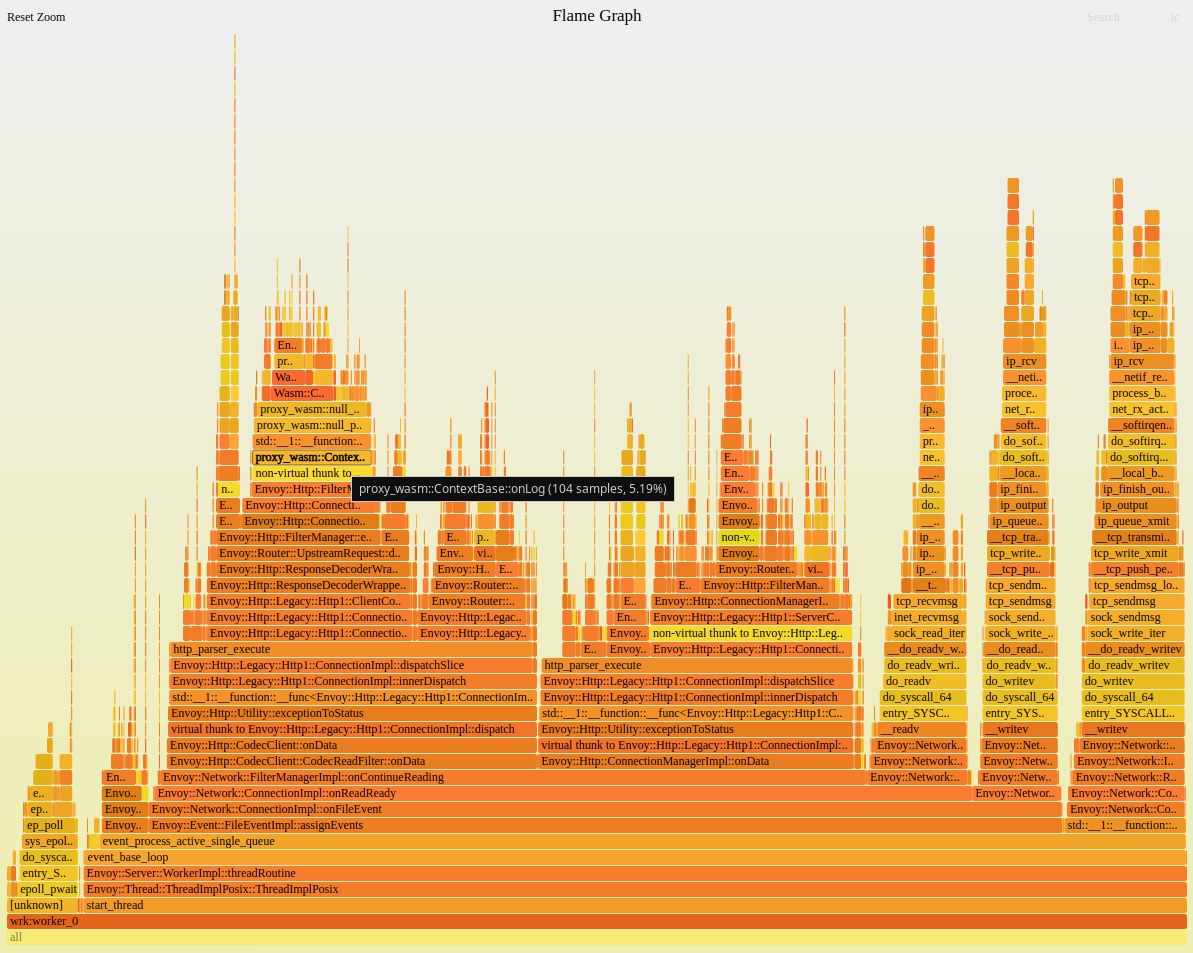
If it takes interest and momentum to push a new technology, then what is needed to get this technology go to live production is hard working. Including Cloud Native and Istio.
In pre-launch performance testing, Istio out-of-box provided observability, operational convenience, and also introduced pain: Increased service latency. How to minimize latency has become a critical task.
My Scenario:
There are two paths under my feet: